Onchain subscription proration unlocks powerful recurring revenue models for SaaS, digital content, and decentralized services. Yet the complexity of prorated billing logic and the immutable nature of smart contracts create a uniquely challenging security environment. Failing to address these risks can result in lost funds, broken trust, or catastrophic protocol failures. Let’s dissect the top five security risks that every developer and auditor must prioritize when building or reviewing onchain subscription proration smart contracts.
![]()
1. Proration Calculation Manipulation: Arithmetic Safety First
Accurate proration is the backbone of fair billing in onchain subscriptions. However, attackers may exploit arithmetic vulnerabilities, such as integer overflows, underflows, or rounding errors, to underpay or overcharge subscriptions. These bugs are subtle but devastating: a single unchecked calculation can drain protocol reserves or unfairly penalize users.
Best Practice: Always use established safe math libraries (like OpenZeppelin’s SafeMath) for all arithmetic operations within your proration logic. Thoroughly unit test edge cases, such as near-zero durations, maximum integer values, and mid-cycle plan changes, to ensure robust handling. Never assume Solidity’s built-in types will protect you; explicit safety checks are mandatory.
2. Oracle and Time Manipulation Risks: Trustworthy Data Sources
Subscription proration often depends on accurate timing, how long a user has subscribed at a given tier determines their bill. Relying solely on block timestamps exposes your contract to miner manipulation, which can skew billing cycles by seconds or even minutes. Worse yet, if you use external oracles for time or price feeds, a compromised oracle could wreak havoc on your entire billing system.
Best Practice: Integrate decentralized oracle networks with aggregation mechanisms to source time and pricing data securely. Avoid using block. timestamp as your sole timing mechanism; consider hybrid approaches that cross-reference multiple sources where possible. For deeper insights into oracle security pain points and solutions, see this resource from Metaheuristic.
3. Reentrancy Attacks on Billing Functions: Guard Your State
The infamous DAO hack taught us that reentrancy is one of the most dangerous vulnerabilities in Ethereum smart contracts, and recurring billing functions are prime targets. If your contract makes external calls before finalizing state changes (for example, when transferring tokens during payment processing), an attacker could recursively trigger the function to drain funds or generate bogus invoices.
Best Practice: Apply the Checks-Effects-Interactions pattern religiously: update internal state before making any external calls. Use reentrancy guards (such as OpenZeppelin’s ReentrancyGuard) on all functions that handle payments or invoice generation. This is especially critical for contracts managing complex flows like mid-cycle upgrades or downgrades where multiple state variables change in quick succession.
Top 5 Security Risks & Best Practices for Onchain Subscription Proration
-

Proration Calculation Manipulation: Ensure all proration logic is resistant to arithmetic overflows/underflows and rounding errors by using safe math libraries (such as OpenZeppelin’s SafeMath) and thorough unit testing. Attackers may exploit calculation flaws to underpay or overcharge subscriptions, so robust validation is essential.
-
Oracle and Time Manipulation Risks: Use secure, decentralized oracles (e.g., Chainlink) or reliable time sources for billing cycles and proration calculations. Relying on block timestamps alone can expose contracts to miner manipulation and inaccurate billing, so aggregation and verification of oracle data is recommended.
-
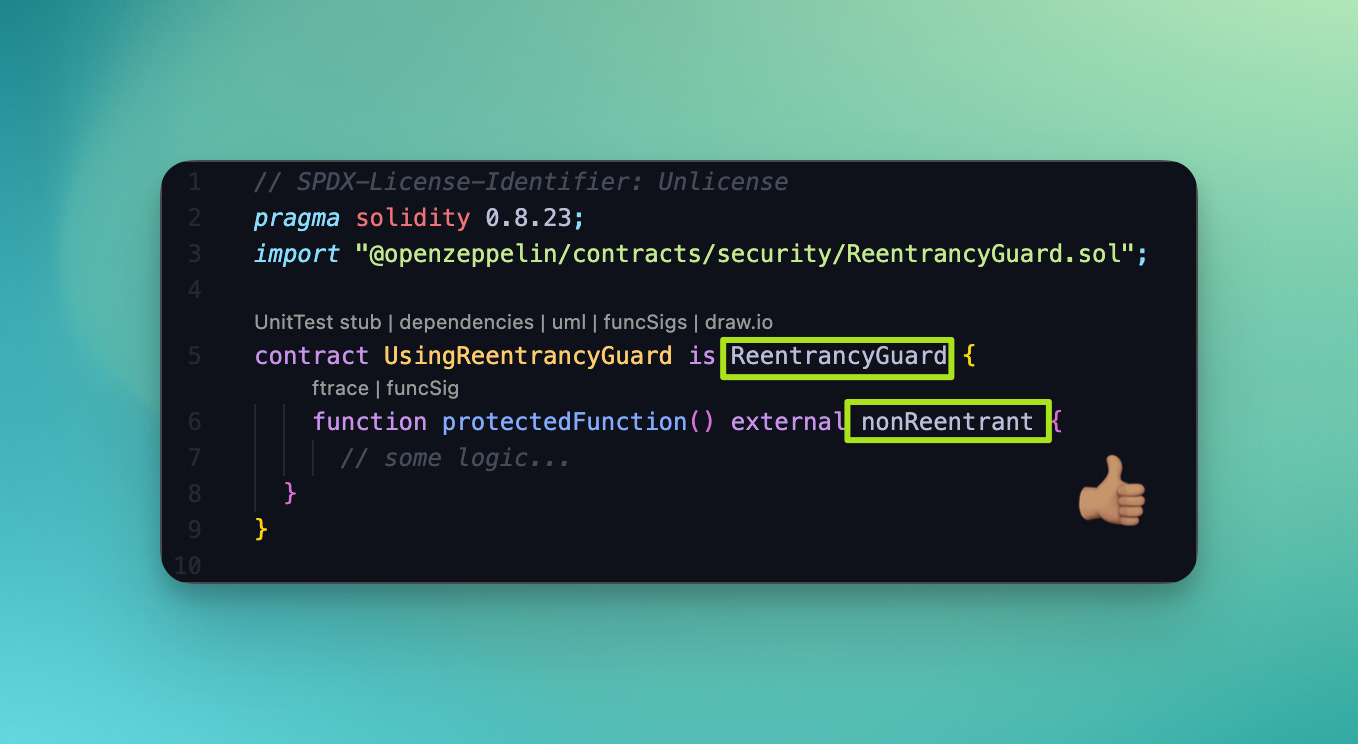
Reentrancy Attacks on Billing Functions: Protect critical functions like payment processing and invoice generation from reentrancy by applying the Checks-Effects-Interactions pattern and using reentrancy guards (such as OpenZeppelin ReentrancyGuard), especially when handling external calls.
-
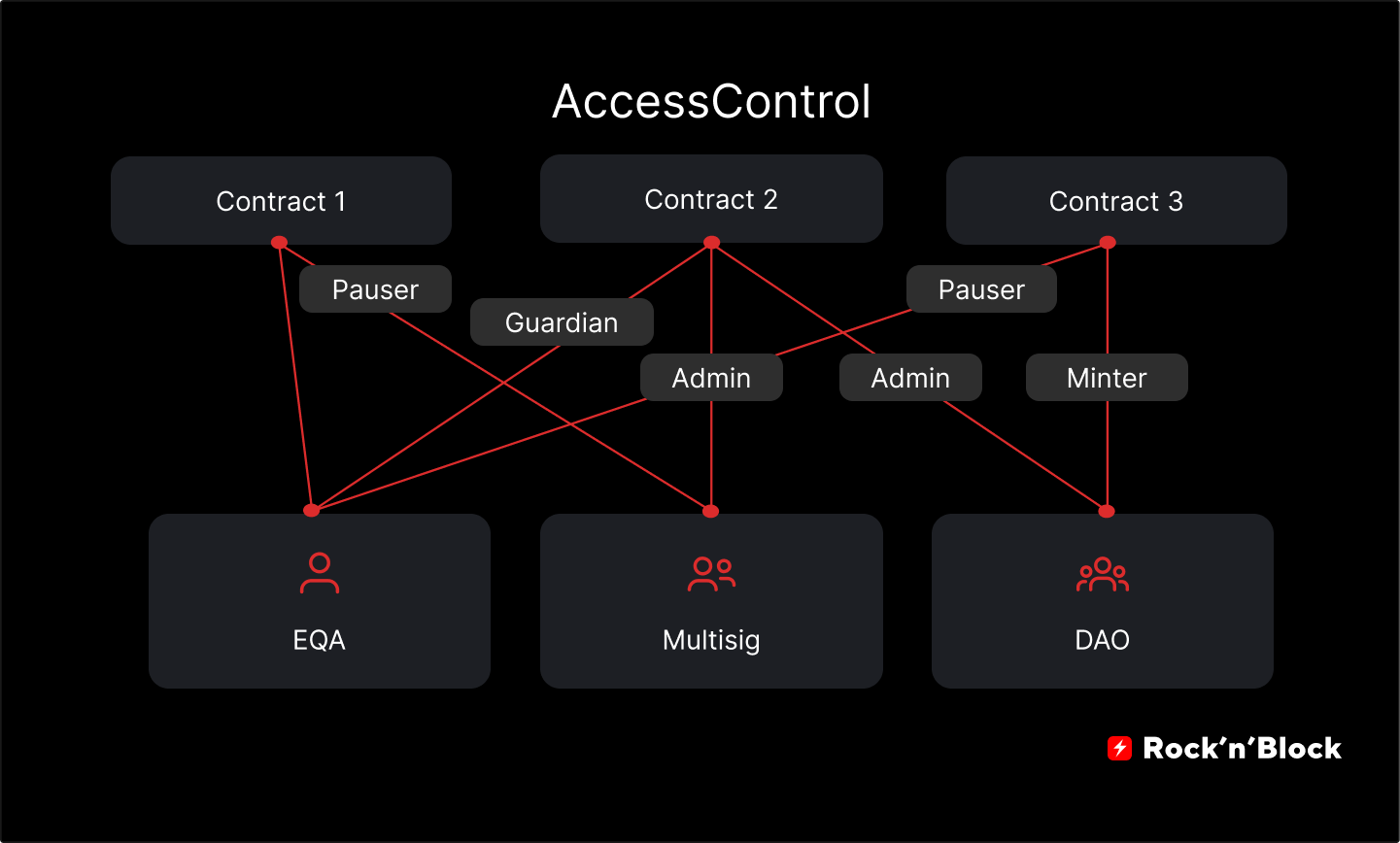
Insufficient Access Controls on Subscription Updates: Restrict who can modify subscription terms, proration parameters, or billing cycles by implementing strict access controls (e.g., only contract owner or authorized roles). This prevents unauthorized changes that could disrupt billing accuracy. Use established libraries like OpenZeppelin AccessControl for robust role management.
-
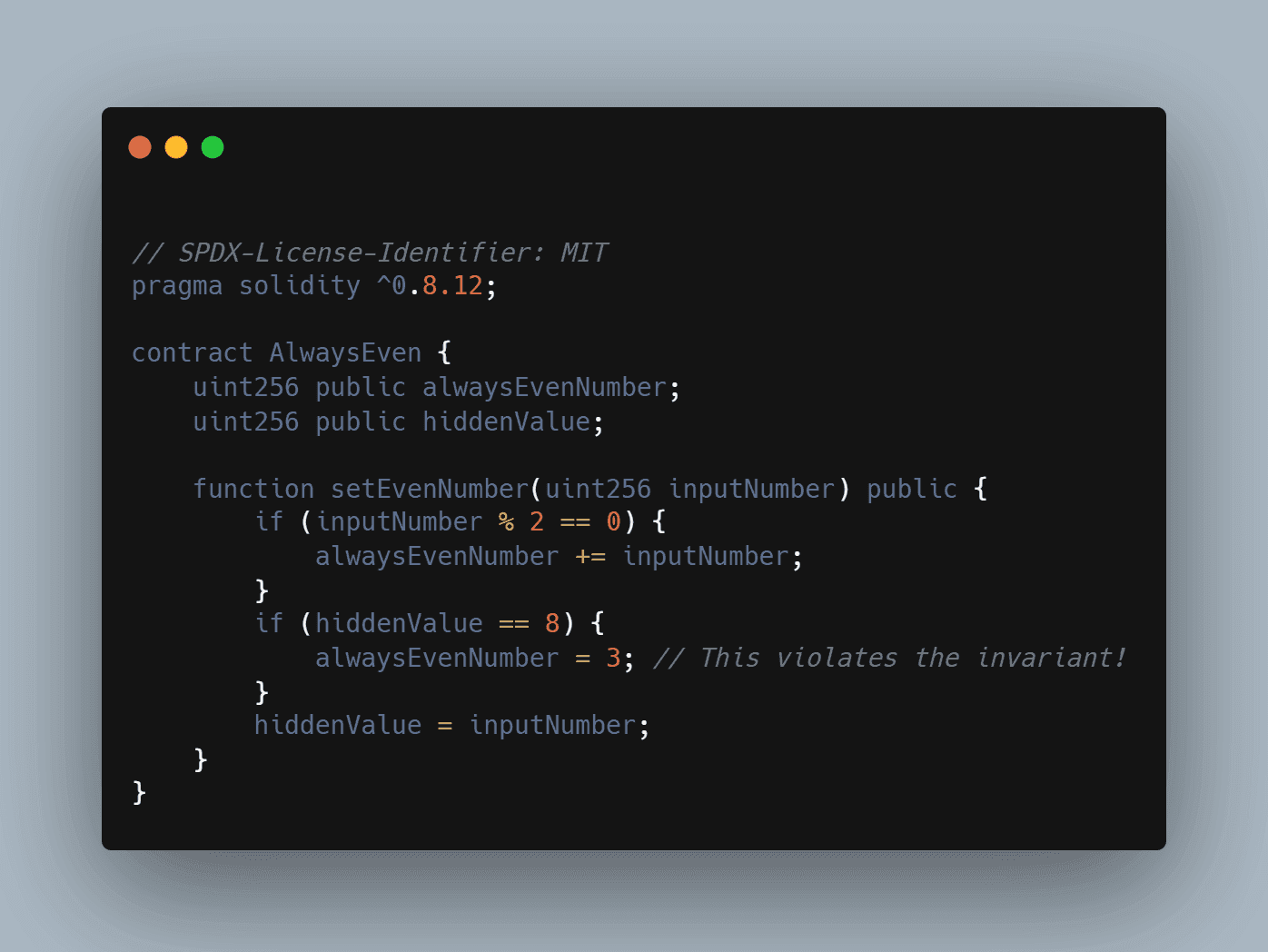
Lack of Comprehensive Audit and Testing for Edge Cases: Regularly conduct security audits focused on complex proration scenarios (e.g., mid-cycle upgrades/downgrades, cancellations) and use automated fuzz testing tools (such as Echidna) to uncover hidden vulnerabilities unique to prorated subscription logic.
The Hidden Complexity of Prorated Subscription Logic
Beneath these headline risks lies an ecosystem of edge cases, mid-period cancellations, plan upgrades/downgrades, refunds, that can introduce subtle bugs if not rigorously tested and audited. In part two of this article, we’ll examine how insufficient access controls and lack of comprehensive testing further expose protocols to manipulation and loss.
4. Insufficient Access Controls on Subscription Updates: Lock Down Critical Functions
Even the most mathematically robust proration logic can be undermined if unauthorized parties can alter subscription parameters, billing cycles, or proration coefficients. Attackers may exploit weak access controls to manipulate user plans, adjust proration settings in their favor, or disrupt service for legitimate users. These vulnerabilities are especially dangerous in decentralized environments where contract code is public and adversaries actively probe for misconfigured permissions.
Best Practice: Implement strict, role-based access control for all administrative functions, such as updating pricing, changing proration formulas, or modifying billing schedules. Use established patterns like Ownable or AccessControl from OpenZeppelin to restrict sensitive operations to the contract owner or explicitly authorized roles. Regularly review and test these permissions during audits to ensure no privilege escalation paths exist.
5. Lack of Comprehensive Audit and Testing for Edge Cases: Audit Beyond the Obvious
The devil is in the details: prorated billing contracts must handle a labyrinth of edge cases, mid-cycle upgrades/downgrades, cancellations with partial refunds, overlapping subscriptions, that rarely surface in simple test scenarios. Overlooking these complexities creates fertile ground for exploits that only manifest under unusual but plausible conditions.
Best Practice: Go beyond standard unit tests by conducting automated fuzz testing and scenario-based integration tests that simulate real-world user behavior across a spectrum of timelines and plan changes. Engage independent security auditors with experience in financial smart contracts to review not just your code but your entire business logic flow. For additional guidance on tailoring audits to complex business requirements, refer to this resource by OnFinality.
A Proactive Security Checklist for Onchain Subscription Proration
Robust security isn’t just about patching bugs after they’re found, it’s about anticipating how attackers might exploit every facet of your recurring billing design. Here’s a concise checklist that development teams should integrate into their workflow from day one:
The rise of blockchain-based recurring billing solutions offers transparency and automation previously impossible in legacy finance, but only if protocols are engineered with uncompromising attention to detail. By proactively addressing arithmetic safety, oracle integrity, reentrancy protection, airtight access controls, and exhaustive testing against edge cases, you position your platform at the frontier of secure crypto recurring payments.
If you’re building or auditing onchain subscription systems with advanced features like proration and dynamic invoicing, make these five priorities non-negotiable pillars of your process. The long-term value, and trust, of your protocol depends on it.